2. Make the name longer until you the program crashes, and you no longer see the "FAIL!" message.
3. Compile the source code below locally, run it in a debugger, and develop an exploit that bypasses the password.
4. Run your exploit on my server and get your name on the WINNERS PAGE! The first ten characters of the name are sent to that page when you win.
Here's the source code. It's accurate, except the real password has been replaced by "password".
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
char name[40], pwd[10];
void win() {
FILE *fp;
char n[11], cmd[60];
strncpy(n, name, 10);
n[10]='\0';
printf("A WINNER IS %s!!\n", n);
fflush(stdout);
system("date >> /var/www/html/bufo-c-winners.html");
sprintf(cmd, "echo \"<big><b>%s</b></big><br>\" >> /var/www/html/bufo-c-winners.html", n);
system(cmd);
}
main(int argc, char *argv[]) {
int i;
strcpy(name, argv[1]);
strcpy(pwd, argv[2]);
printf("win() at: %08x<p>\n", win);
fflush(stdout);
if (bo() == 0) win();
else printf("FAIL!\n");
}
int bo() {
char buffer[10];
strcpy(buffer, name);
if (strcmp(pwd,"password") == 0) {
return 0;
}
else {
return 1;
}
}
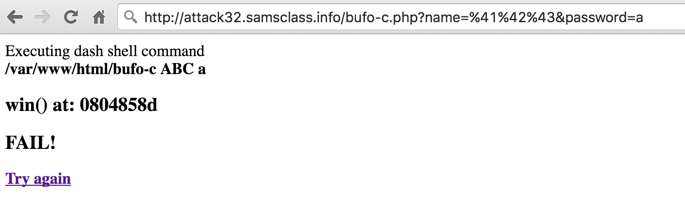
An easy way to send non-ASCII characters is to use the URL bar in the page you see after clicking the Execute button, like this: